2024 Data Breach Investigations Report
Learn about the latest trends in real-world security incidents and breaches—to help protect your organization and help you evaluate potential updates to your security plan.
Top takeaways
Explore a preview of some of the cybersecurity data uncovered by this year’s DBIR.
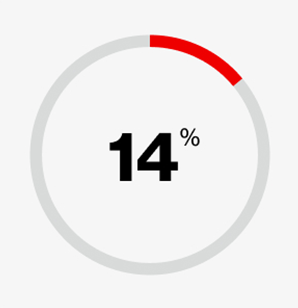
of breaches involved the exploitation of vulnerabilities as an initial access step, almost triple the amount from last year’s report
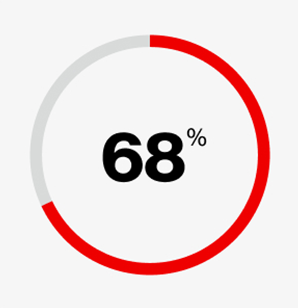
of breaches involved a non-malicious human element, like a person falling victim to a social engineering attack or making an error
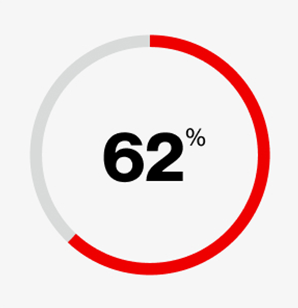
of financially motivated incidents involved ransomware or extortion, with a median loss of $46,000 per breach
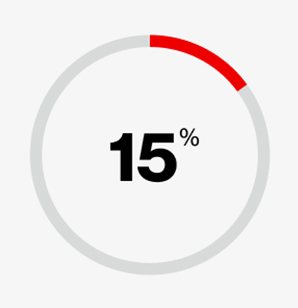
of breaches involved a third party or supplier, such as software supply chains, hosting partner infrastructures or data custodians
Key resources
2024 DBIR
Access the full report for a highly trusted, comprehensive view of cyber threats and data breaches.
2024 DBIR executive summary
Explore report highlights, including the latest breach findings for various industries and regions.
2024 DBIR infographic
Get data about recent security incidents at a glance to help protect your organization.
2024 DBIR SMB infographic
Understand the latest threats to small and medium businesses to help protect your people, assets and reputation.
Breaking down the 2024 DBIR
Listen to security expert Chris Novak break down data from this year’s report, and discuss how to prepare for and mitigate data breaches.
Snapshots

Webinars
Our experts discuss the latest cyber threats and how organizations can evaluate their cybersecurity preparedness.
2024 DBIR Key Findings
Join the DBIR authors as they discuss real-world cybercrime and how cyber attacks affect organizations of all sizes across the globe.
2024 DBIR: Apply the Findings
Learn from our cybersecurity experts as they break down recent cyber threats and discuss how you can help protect your organization.
Security report archive
2023 DBIR
Read our detailed analysis of 16,000+ global security incidents to help strengthen your cybersecurity awareness. Download the report.
2022 DBIR
Gain vital insights from our analysis of 23,000+ cybersecurity incidents from around the world. Download the report.
2021 DBIR
Learn when to engineer security solutions and when you can rely on your security operations. Download the report.