2025 Data Breach Investigations Report
Today’s threat landscape is shifting. Get the latest updates on real-world breaches and help safeguard your organization from cybersecurity attacks.
Key resources
Top takeaways
Explore eye-opening stats and critical findings from this year's report.
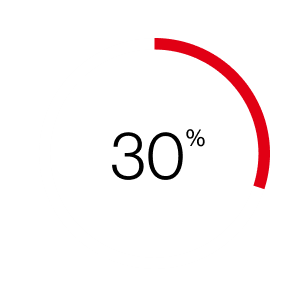
of breaches were linked to third-party involvement, twice as much as last year, and driven in part by vulnerability exploitation and business interruptions

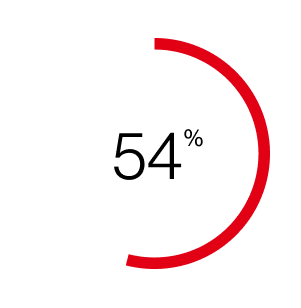
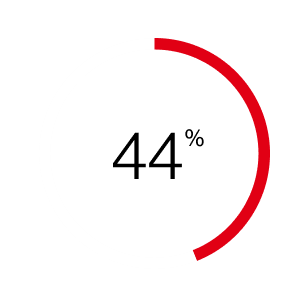
increase in attackers exploiting vulnerabilities to gain initial access and cause security breaches compared to last year's report
Watch our latest webinar series
Learn from renowned cybersecurity experts as they reveal the latest threats uncovered in the 2025 DBIR, along with innovative strategies to help combat them.
2025 DBIR Key Findings
DBIR authors take a deep dive into the 2025 report. Gain crucial insights on emerging cybersecurity threats and attack strategies across organizations and industries.
2025 DBIR: Turning Insights Into Action
Learn from our expert panelists as they share proactive defense strategies and best practices to help mitigate risk and strengthen your organization’s security posture.
Be first to get the latest
Sign up to learn more about this year's DBIR and get key updates on cybersecurity.
Explore the archive
2024 DBIR
Learn how to prepare for cybersecurity threats, no matter the size of your organization. Review real-world breaches to help evaluate potential updates to your security plan.