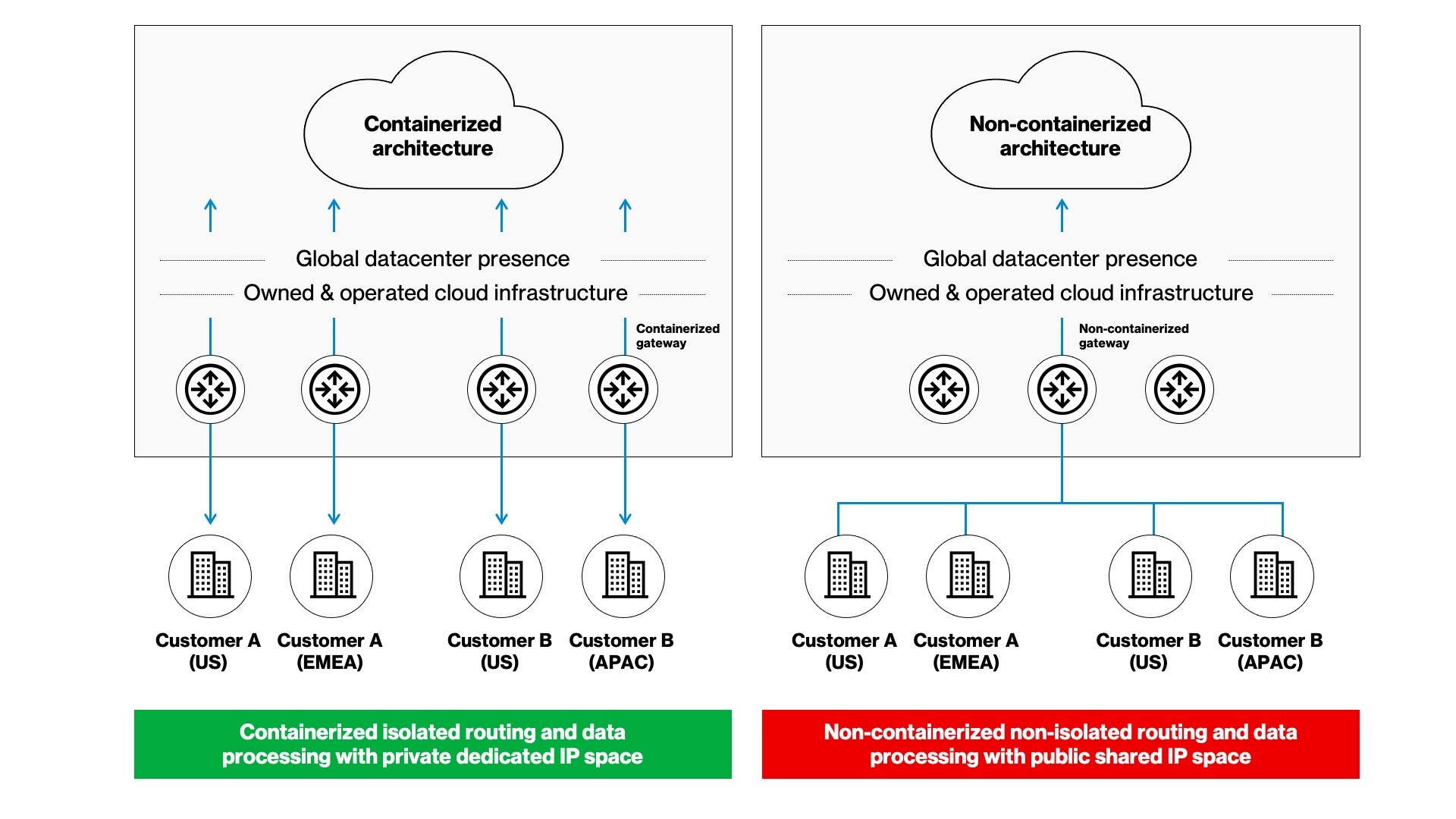
Companies are moving to a ‘Zero Trust’ model of cyber security which takes the approach that no users or devices are to be trusted without continuous verification, while limiting potential system response latency. With mobile and remote office workers now using cloud-based applications, businesses need to protect weaknesses around the network perimeter, as well as fragmented network traffic that are vulnerable to attacks.
Verizon’s Zero Trust Dynamic Access provides a zero trust cloud security solution for secure access to the open internet, cloud applications, private applications and data, and public cloud services. that helps you defend your business. Acting as both a first and last line of defense, this service protects users, apps, and data on any device, while maintaining performance and eliminating the need to backhaul traffic or use Virtual Private Networks (VPNs). At Verizon, we help you keep up with rapidly changing cyber threats by processing more than one million security events every day at our global network operations centers and security operations centers.